

Your personal information is a valuable resource that is desirable on all sides. On one hand, huge websites like Google and Facebook are attempting to collect your information and sell it to third parties for targeted advertising. Further, cybercriminals and hackers want to gain access to your data to sell it on the Dark Web.
In this intimidating and daunting digital world, an increasing number of internet users are searching for solutions to browse the internet anonymously and safely. One of these solutions is the TOR software.
What is TOR Browser?
Tor stands for The Onion Router and it is named so because of the way it protects your information by enfolding it in many layers of encryption just like an onion. Tor can considerably enhance the anonymity and privacy of users online.
Tor is open-source and free software that allows using the internet anonymously. When you use the Tor browser to surf the internet, your traffic is sent arbitrarily using a network of servers before it approaches the final point to secure your identity and location.
Tor browser is like a common web browser in various ways. It is similar to Microsoft Edge or Google Chrome and is not difficult to use. The difference between Tor and a normal browser is that it connects you to the internet using the Tor network.
How Does Tor Work?
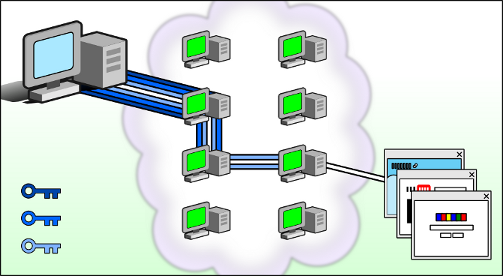
The Tor Browser directs your internet traffic using the Tor Network to make it anonymous. Tor network consists of three-layer protection, just like multi-layers of an onion. The motivation behind the Tor logo comes just from here.
When you browse using the tor browser, your information moves over various Tor servers also known as nodes. While traveling the web traffic is highly encrypted and secured, and is decoded at the other node one layer after the other.
If anyone attempts to recognize you depending on the web traffic, they will only know the last server or last TOR node where your data traveled, making it difficult for anyone to identify its users. Using the Tor browser, no matter what you do online, everything will be encrypted and your anonymity would be intact.
The only problem with the Tor browser is that it is much slower as compared to normal internet browsers. It is because your data traffic sends and receives through several nodes.
Is Tor Browser a VPN?
Some people may have questions in mind like; is Tor browser a VPN? Or Tor browsers and VPN work the same? The answer is they are not the same but both of them are different tools to protect your online privacy.
A VPN is used to protect and secure your online data with end-to-end encryption. Then the data travels using a safe tunnel to a remote server that helps you connect to the website you are trying to reach.
On the other hand, the Tor browser works differently to protect your privacy that is explained in the above section.
The most important thing to remember is that you can use both VPN and TOR in combination to enhance your privacy and security.
How Secure is Tor Browser?
Tor browser effectively hides your location and prevents your internet traffic from being traced. Your online activity can’t be tracked through Tor’s network back to you. However, the Tor browser is not 100% secure. The browser has some drawbacks. As each server or node in the Tor network is operated by a volunteer, you are unaware of who is behind the relays, your information moves through.
Generally, it is not a big problem as every TOR relay can reach only the location of the next and previous relays, excluding the TOR exit node. At the exit node, the last layer of encryption on your information will be removed. This cannot reach out to your real IP address or location but the TOR exit node can spy on your action if you use an unsafe HTTP website.
Similar to other browsers, tor browser is also susceptible to similar attacks and cyber threats. It is a great idea to turn-off plugins of the browser if you want to keep your anonymity intact as these can be used to disclose your data like your IP address.
How do I use Tor?
You can use Tor browser similar to standard web browsers and surf the internet easily. Simply go to Tor’s official website and download it. For installation, follow the guidelines given on the website just like you do for any other software.
When it is installed, you are ready to launch the Tor Browser. When you first open it, the browser will ask you to either connect simply or configure your connection. When you click on the connect option, Tor may take some time to look for a collection of relays to connect you with.
However, when it is all set and you are in, you can use the Tor browser just like any other browser. Tor browser will also ask you to review its security settings. If you want maximum security, it is recommended to leave the settings on the default mode.
If you feel the speed is slower than normal, you can push Tor into action by looking for a fast connection route to the site you are trying to visit. Click the three line icon on the top right area of the Tor browser and choose New Tor Circuit for this Site.

Leave a Reply