
Beyond VPNs: 10 Alternative Methods to Protect Online Privacy
In today’s digital age, protecting online privacy has become increasingly crucial. While Virtual Private Networks (VPNs) have been a popular choice for many, they aren’t […]

In today’s digital age, protecting online privacy has become increasingly crucial. While Virtual Private Networks (VPNs) have been a popular choice for many, they aren’t […]

As artificial intelligence and natural language processing technologies continue to evolve, we are seeing an increasing number of malicious threat actors leverage these tools for […]

ChatGPT is a state-of-the-art language model developed by OpenAI that is designed to perform various natural language processing tasks such as text classification, language translation, […]


Malware is any piece of software that was created to harm devices, data, and people. Malicious software is written with malicious intent. If malware infects […]

We all find it convenient to do online shopping. Even though it has become a popular choice for customers to save money and time, it […]
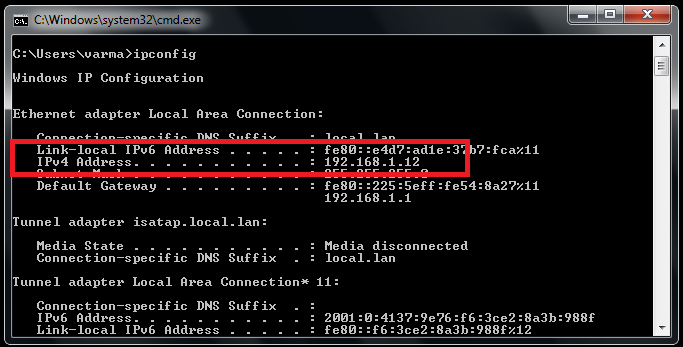
Here are some of the TCP/IP commands and their functions described briefly. Some of the commands are used to configure and diagnose your network. Keep in mind while writing from the command swift you can only write one command on each line and press the “Enter” button after each command to implement it. Arp, ipconfig, nslookup, ping, etc.
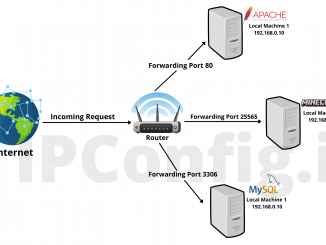
Whether you are hosting a trivial website or making a game available to other people, port forwarding is a great method to access software operating […]

What is Social Engineering Attacks? Social Engineering Attack is a process of manipulating people to force them to give their personal or confidential information and […]

Parents want their kids to use the Internet, then they should properly understand the usage status and use filtering software or other methods. It is […]
Copyright © 2025 | WordPress Theme by MH Themes