
Have you ever received an email that appears as it came from your bank with a warning that if you didn’t verify your personal information, your account will freeze? The email may contain a link and if you click that link you may land on a site that requested you to fill in the details like bank account number and any personal identity number such as Social Security number or any other private information.
Here is the problem. Such emails don’t come from a real bank. Rather than that, they are a component of a scamming tool known as phishing used by cyber attackers or cybercriminals and a risk to your online security and online privacy.
What is Phishing?
Phishing involves an attempt to collect your personal information with the help of misleading and false emails and websites. The main goal of attackers is to trick or mislead the recipient of the email to believe that the message is from a real source i.e. a message from their bank or a letter from their company and asking to click on a link or download an attachment.
The major sign of phishing is that the attacker pretends to be a trusted entity, mostly a real or possibly real person or an organization the recipient might do business with. Phishing is a very old form of a cyber-attack, originated in the 1990s and it is one of the most prevalent and well-known cyber-attacks.
Attackers also use phishing to encourage targets to download an attachment or click on a link that installs the malicious content that could distribute ransomware, Trojan malware, or other kinds of disruptive or damaging attacks.
How does Phishing work?
You need to know that anyone who’s using the internet or smartphone can be the target for a phishing attack. Phishing attacks usually involve:
- Stealing your personal information and credentials to access your identity or money
- Infecting your computer or phone with malware
- Convincing you to send valuables or money
- Obtaining control over your online accounts
At times such phishing attacks don’t stop at you. If a scammer successfully gets into your contact list or social media accounts, they may scam people you know with such messages that seem to be coming from you. Urgency and belief are what make phishing so dangerous and deceiving.
Protect Yourself from Phishing Attacks
The first line of defense against phishing emails is the email spam box that filters phishing emails from your inbox. However, scammers try to beat the spam filter, so there is a need to protect your cybersecurity by adding extra layers of protection. Following these four steps, you can keep yourself protected from phishing attacks.
Steps to Protect Yourself from Phishing
- Do not click on any links listed in the email message, and do not open any attachments contained in a suspicious email. Instead hover your mouse cursor over such links and look for anything suspicious such as a fake domain name or if the URL has HTTPS in the beginning.
- Do not enter personal information in a pop-up screen.
- Don’t Use the Same Password Everywhere. Instead use Password Manager and generate different, random and strong passwords for every website.
- Use security software to protect your computer. Set it at auto-update so that it can tackle new threats.
- Use security software for your mobile and protect it from cyber-attacks. Set it on auto-update mode so that it offers the necessary protection against security threats.
- Use multi-factor authentication to protect your online accounts. Multi-factor authentication will make it difficult for attackers to access your accounts even if they know your user ID and password.
- Backup your data for protection and ensure that the backups are not linked to your home network. You can save it on cloud storage or copy it on an external hard drive. Also, backup your phone data.
Real Life example of Phishing attack.
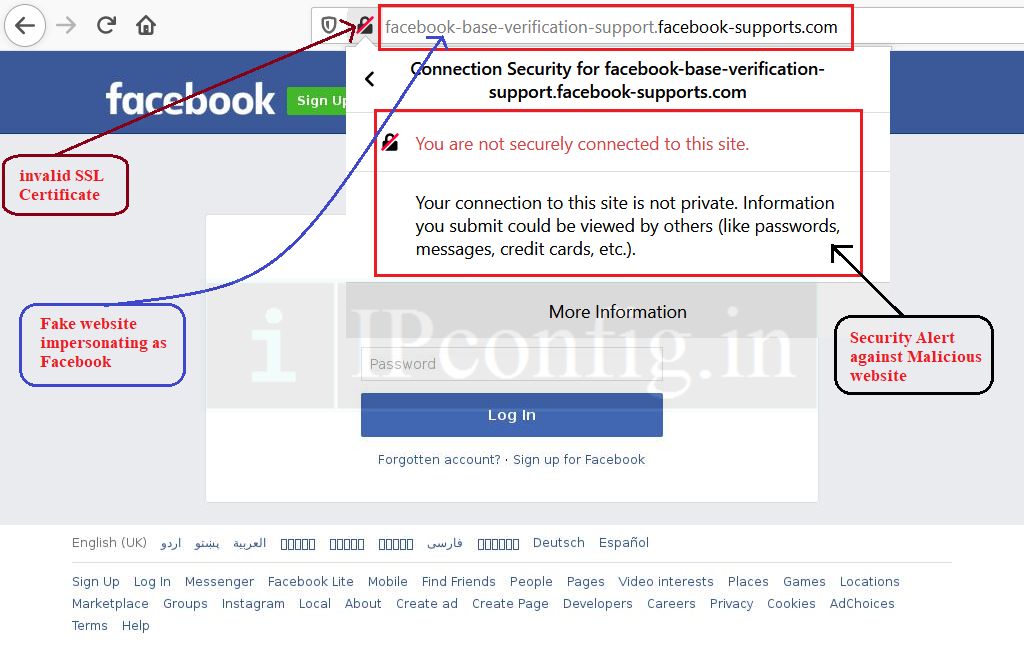
Above image is a screenshot of Phishing page created to steal login and Password of Facebook. We can identify that that this is not the legit Facebook.com website by looking at the URL which is not the official facebok.com domain. Also, it is not using the valid SSL certificate and running on HTTP and not on HTTPS.
What is vishing?
Vishing is a type of phishing, where a scammer uses a phone call or direct chat message instead of an email or a text message. Scammers use phone calls that appear like they are from a trusted source but they are not. The goal of a vishing call is to steal your money or identity.
A scammer uses a vishing call to urge you to share your private credentials and financial details like passwords, security numbers, or account numbers. The scammer will use some tricks to convince you like they may claim to be your bank, or offer to help you install the software. You need to know that it could be malware.
Today, it is easier than ever to contact more people. Scammers can call hundreds of people at the same time using VoIP technology and can transform the caller ID to show like it is coming from a trusted source, like your bank.
Protect yourself from vishing
Here are some simple tips which you can use to protect yourself from vishing:
- You may be tempted to answer all the phone calls but you need to let calls from unknown numbers go to voicemail. You may not know who is calling as the caller IDs can be faked. After listening to messages, you can decide whether to call that person or not.
- If a person gives you a number to call back, it can also be a scam, so be careful before using it. Instead, look for the official contact number of the organization and call the company in question.
- When you realize that this is a vishing call, you don’t have to carry on the call and talk politely. Just hang up the call and simply block the number.
- If you receive any message that prompts you to respond to questions or press buttons, don’t do it. For example, the message might say “Type ‘yes’ to talk with an operator.” Scammers frequently use such tricks to recognize targets for more robocalls. They can also record your voice to use it while routing voice-automated phone menus linked to your online accounts.


Leave a Reply