In the last few years, we have seen a rise in the number of sites that lose the personal data of their users. With the sophistication of cybercrime, many companies have seen their security protocols outdated that don’t match the modern attacks and threats. It is not only the user’s trust that can be scratched. All sorts of companies whether big or small face serious reputational and financial loss due to data theft by hackers or cybercriminals.
When we talk about a user like you, the results of identity theft or targeted hack can be distressing. They use your stolen information to secure bogus credit cards which can badly harm the credit rating of the victim. Even the cryptocurrency accounts and an entire bank can be emptied overnight.
Online websites and mobile applications must provide appropriate security to protect our identity and credentials. Further, users themselves need to make a habit of protecting their data by using something more powerful than a password. Many choose 2 Factor Authentication to add an extra layer of security to their personal data.
Why do I need 2 Factor Authentication – 2fa?
Generally, the passwords we use to protect our online accounts are weak because of the advanced ways of hacking as well as the annoying process of creation and use of the password. Most of us feel it convenient and easy to use the same password for securing many accounts but it actually increases the susceptibility of attacks and chances that criminals figure out your identity and credentials.
When you use a very simple or common password like 123456, or 111111, it becomes extremely easy for criminals or attackers to figure out your password by using methods like Brute Force attack. Also, when you use the same password on multiple different online services, attackers use Credential Stuffing attack. In the Credential Stuffing attack, attackers use a combination of Email and password or Username and Password, obtained from publicly available breached databases. It may feel stressful to add another step of verification to your browsing or web surfing, but it is necessary if you don’t want to leave yourself exposed to cybercriminals looking to snip your personal details, bank account information, or gain access to your credit card online portals.
The addition of an extra verification step simply means more struggle from criminals to gain access to your personal details. For instance, if you use 2-factor authentication to secure your bank account, an attacker who knows your passcode wouldn’t be able to reach out to your account because he/she won’t have access to your phone when it gets the verification code such as OTP – One Time Password.
This is the reason for having a 2 Factor Authentication for online accounts. So you must not rely only on the password and go for 2 FA as it keeps your identity secure better than a simple password.
What is 2 Factor Authentication?
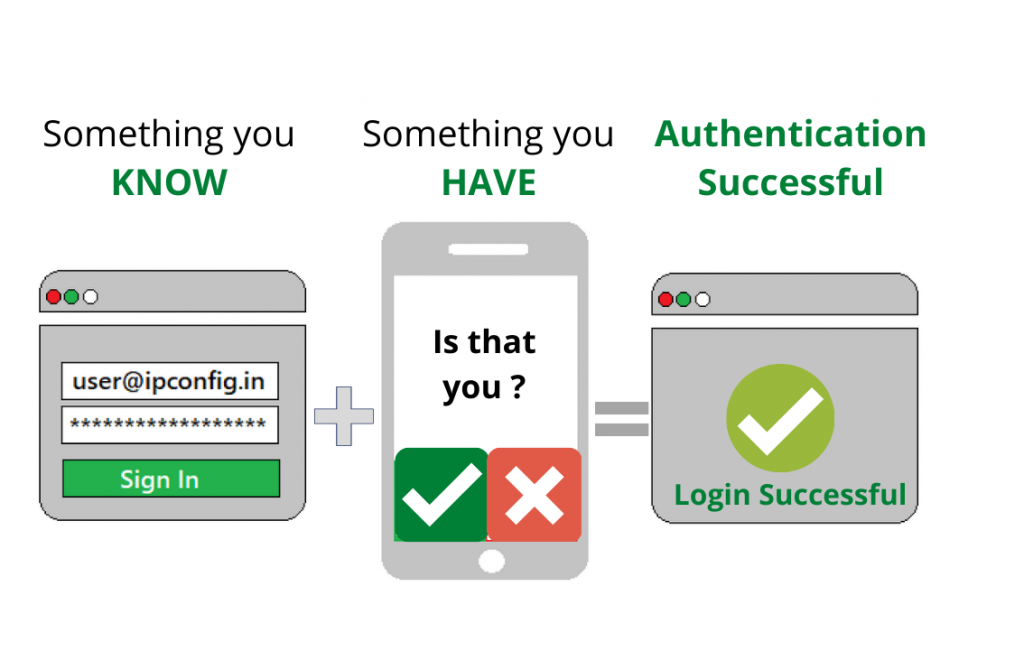
Now we know why we need 2 Factor Authentication and what is its importance, let’s learn about what exactly is 2 Factor Authentication.
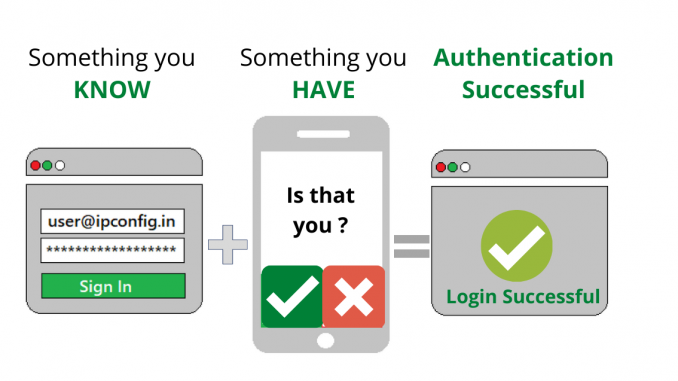
In simple words, it is an additional step of verification added to the sign-in process for different online accounts. It can be like a simple code sent to your smartphone, or a fingerprint scan that is needed to confirm your identity and minimize hacker’s attacks and cybercriminals unwanted access to your personal identity.
The 2 Factor Authentication adds an extra layer of security that is not easy to access by cybercriminals as they will require more information other than just username and password. It is named so as it needs a combo of 2 factors likewise multi-factor authentication needs more than 2.
First of all, a user needs to add the username and password to log-in to the account. But rather than getting access to the account immediately, the system will ask you to give another piece of information. The second factor for gaining access can be one of the following:
- Something you have
Generally, people choose their second-factor information from something they keep like a smartphone, a credit card, or a small hardware token
- Something you know
It can be a password, a PIN code or answer to a secret question, or maybe a particular pattern.
- Something you are
This is a bit advanced category and includes biometric verification of a fingerprint, a voiceprint, or an iris scan.
With 2 Factor Authentication enabled, your account will not be unlocked with a single password. Therefore, even if your mobile phone is lost or the password is stolen, there will be very low chances of someone knowing your second-factor information. Let’s take it the other way around, if you use 2 Factor Authentication in the right way, apps and sites will be assured of your identity and unlock the account.
How secure is 2FA?
You may have a question in your mind about the level of security provided by the 2 Factor Authentication procedures. Unfortunately, nothing can offer 100% security to your identity online. There are ways that cybercriminals and hackers can use to evade the system and reach your account details even with 2-factor authentication enabled.
For instance, recovery of your lost password mainly uses email to reset the password and it can entirely dodge 2 Factor authentication security. However, creating a shield to restrict criminals from accessing your accounts is far better than keeping your accounts open for cybercriminals by not enabling 2 Factor Authentication.
Make it difficult for cybercriminals and hackers to attack your accounts, let them look for more information than just username and password to access your accounts by using 2 Factor Authentication. With the growing technology, protecting online privacy is becoming more important and with the help of 2 Factor Authentication, you can protect your privacy to a great extent.

Leave a Reply