In the ever-evolving landscape of cybersecurity threats, the ShinyHunters hacking group has emerged as a formidable adversary. Known for their sophisticated social engineering tactics, they have successfully targeted major corporations, causing significant data breaches and financial losses. This article delves into the methodologies employed by ShinyHunters, examining their impact on companies like Google, Coca-Cola, and Adidas, while providing actionable insights on protecting against such threats–in simple language.
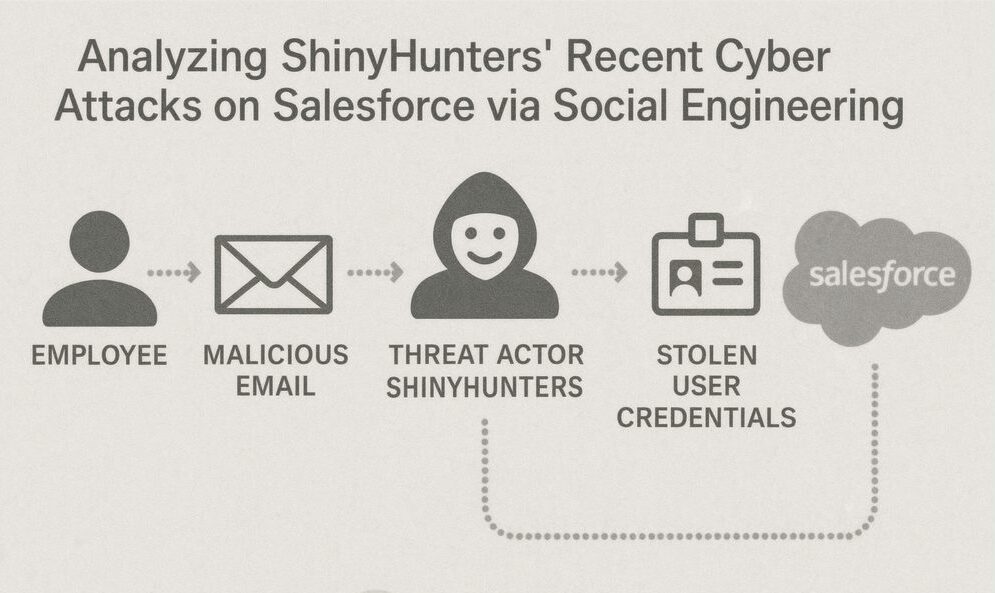
At a Glance
- Shinyhunters have targeted Salesforce using social engineering techniques.
- Their methods exploit human psychology to gain unauthorized access.
- Major companies like Google and Coca-Cola have been targeted.
- Salesforce account breaches highlight the value of customer data.
- Phishing and pretexting are common tactics used by attackers.
- Prevention requires a combination of employee training and robust security protocols.
- Salesforce offers built-in security features that can mitigate these risks.
- Regular audits and updates are crucial for maintaining security.
- Advanced tools and security protocols enhance organizational defense.
- Real-world incidents show the need for comprehensive cybersecurity strategies.
Introduction to Shinyhunters and Their Cyber Attacks
Who are ShinyHunters?
ShinyHunters is a notorious hacking group that gained prominence in 2020. They have been linked to multiple high-profile cyber attacks, leveraging social engineering to infiltrate corporate networks and exfiltrate sensitive data. Their operations are characterized by meticulous planning and execution, often involving multi-step processes to maximize impact and minimize detection. As per available reserach, ShinyHunters is linked with “Scattered Spider” And “Scattered Lapsu$”.
Overview of Recent Cyber Attacks
Recent activities attributed to ShinyHunters include breaches of major companies, exploiting vulnerabilities in corporate cybersecurity frameworks. Their tactics often involve phishing campaigns and credential stuffing attacks, which target weak links within organizational defenses, such as untrained employees and outdated security protocols. By targeting human weaknesses rather than technical flaws, they have successfully infiltrated numerous high-value targets. Apart from these, this group also buys network access as well as data from Access-Brokers of underground darknet sources.
Understanding Social Engineering in Cyber Attacks
Defining Social Engineering
Social engineering is a manipulation technique that exploits human psychology to gain unauthorized access to information or systems. By manipulating emotions such as fear, curiosity, or urgency, attackers can bypass technical defenses. Employees, often the weakest link in security, can be duped into divulging passwords or clicking on malicious links without realizing the implications..
Common Techniques Used in Social Engineering
Some prevalent social engineering tactics include phishing, pretexting, baiting, and tailgating. These methods are designed to trick individuals into divulging confidential information or granting access to secure systems. For instance, phishing involves sending emails that appear to be from legitimate sources, urging recipients to click on malicious links or attachments.
- Phishing: Sending fraudulent emails to trick recipients into revealing sensitive information.
- Pretexting: Creating a fabricated scenario to obtain personal data.
- Baiting: Luring victims with an attractive offer to steal information or install malware.
- Tailgating: Gaining physical access to secure areas by following authorized personnel.
- Quid Pro Quo: Offering a service or benefit in exchange for information.
Step-by-Step: How Social Engineering Attacks Unfold
- Reconnaissance: Attackers gather information about the target organization and its employees via social media, public records, and company websites.
- Building Trust: Using gathered information to pose as trusted entities, attackers engage in preliminary communications to establish credibility.
- Exploit Interaction: Initiate contact through email, call, or text, often with a sense of urgency to prompt quick actions without verification.
- Information Gathering: Through conversation, attackers extract sensitive information or credentials, often using pretexting to justify their requests.
- Access and Infiltration: Use collected information to bypass security measures and access protected systems or data.
- Data Exfiltration: Transfer sensitive data out of the organization’s systems, often using encrypted channels to avoid detection.
- Cover Tracks: Erase signs of the breach, such as deleting logs or disabling security alerts, to avoid immediate detection.
- Monetize Data: Sell or use exfiltrated data for financial gain, often through darknet markets or directly to competitors.
- Analyze Response: Observe the organization’s response strategy to refine techniques for future attacks.
- Repeat: Launch subsequent attacks using refined techniques, targeting other departments or related entities.
Case Studies: Companies Recently Targeted by ShinyHunters
Google: A High-Profile Target
In a notable attack, ShinyHunters managed to breach Google’s data defenses, accessing sensitive user information. This incident highlighted the group’s capability to target even the most secure systems using social engineering. The attackers employed a combination of phishing emails and fake login pages to harvest employee credentials.
Adidas: How the Attack Unfolded
The Adidas cyber attack involved a sophisticated phishing campaign that compromised employee credentials, leading to unauthorized access to internal systems and customer data. Attackers posed as senior executives and requested urgent actions, exploiting the trust and authority dynamics within the company.
Coca-Cola: Breach Details and Impact
The Coca-Cola security breach orchestrated by ShinyHunters resulted in the exposure of proprietary data and employee credentials. The attack underscored the vulnerabilities inherent in corporate cybersecurity strategies, with the attackers leveraging insider information and sophisticated phishing tactics to gain access.
Problem: Coca-Cola faced a significant breach when ShinyHunters targeted their internal systems through a well-executed phishing campaign.
Approach: The attackers used email masquerading as internal IT support to distribute malware that captured employee credentials. This malware was disguised as a routine software update, effectively bypassing initial security checks.
Outcome: The breach led to the exfiltration of proprietary formulas and internal communications, prompting a comprehensive review and overhaul of Coca-Cola’s security policies and training programs. This included the introduction of mandatory cybersecurity workshops and the deployment of enhanced email filtering systems.
The Impact of Shinyhunters on Salesforce Accounts
Details of the Salesforce Breach
In their recent campaign, Shinyhunters exploited Salesforce’s user trust by crafting convincing phishing emails that appeared to be legitimate Salesforce communications. This allowed them to capture login credentials and access sensitive data. Once inside, they could extract valuable information, manipulate data, and even disable security measures to cover their tracks.
Why Salesforce Accounts are Valuable
Salesforce accounts are a treasure trove of customer data and business intelligence, making them prime targets for cybercriminals. These accounts contain valuable insights into customer behavior, sales forecasts, and strategic business plans, which can be exploited for competitive advantage or sold on the black market.
The breach led to unauthorized access to customer data, resulting in financial losses, reputational damage, and potential regulatory penalties for the affected organizations. The exposure of confidential information not only affects the company’s integrity but also erodes customer trust and loyalty.
Consequences of Breached Accounts
The breach of Salesforce accounts can result in unauthorized access to sensitive data, financial losses, and compromised business operations. Beyond immediate financial impact, such breaches can erode trust with clients and partners, necessitating costly remediation efforts and potential regulatory fines.
Strategies to Protect Against Social Engineering Attacks
Identifying Social Engineering Attempts
Organizations must educate employees to recognize signs of social engineering attempts, such as unsolicited requests for personal information or urgent actions demanded through suspicious emails. Awareness is the first line of defense against these types of attacks.
Training Employees to Recognize Threats
Regular training sessions and simulated phishing exercises can enhance employee awareness and response to potential threats. Training should include recognizing phishing emails, suspicious phone calls, and unusual requests for sensitive information. Employees who are well-informed can act as human firewalls, detecting and reporting suspicious activities.
Implementing Stronger Authentication Methods
Adopting multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for attackers to gain unauthorized access. Organizations should also consider biometric authentication and adaptive authentication techniques based on risk assessment. These measures ensure that even if credentials are compromised, unauthorized access is thwarted.
Strengthening Salesforce Security
Best Practices for Salesforce Security
- Enable MFA for all Salesforce accounts.
- Regularly update passwords & use complex passphrases and password manager.
- Monitor login activity and set up alerts for suspicious behavior.
- Utilize IP whitelisting to restrict access to trusted networks.
- Conduct regular security assessments and penetration tests.
Utilizing Salesforce’s Built-in Security Features
Salesforce provides robust security features, such as IP whitelisting and session management, which can be configured to enhance account protection. Administrators should enable these features and regularly review audit logs to detect anomalous activity. Consistent monitoring can preemptively identify unusual patterns that may indicate a breach.
// Example: Enabling IP Restrictions in Salesforce
Setup -> Network Access -> New
Enter Start IP Address and End IP Address
Save
Regular Security Audits and Updates
Conducting regular security audits and keeping software up-to-date are critical practices to identify and mitigate potential vulnerabilities. Organizations should establish a routine for reviewing security logs and updating security patches promptly. This proactive approach helps in addressing potential threats before they are exploited by malicious actors.
Unified Comparison: Security Measures & Social-Engineering Defenses
| Measure / Strategy | Effectiveness | Implementation Complexity | Cost | Benefits | Challenges |
|---|---|---|---|---|---|
| Employee Training | High | Medium | Medium | Improves awareness and reduces risk of successful attacks. | Requires ongoing commitment and resources. |
| Multi-Factor Authentication (MFA) | Very High | Low | Low | Provides an additional layer of protection. | Can be cumbersome for users if not implemented smoothly. |
| AI Threat Detection | Very High | High | High | Detects anomalies at scale, speeds response, can surface unknown threats. | Needs quality data and tuning; skilled staff; potential false positives. |
| Regular Security Audits | Medium | High | Medium | Identifies potential vulnerabilities and areas for improvement. | Can be resource-intensive and requires expertise. |
| Incident Response Planning | High | Medium | Medium | Ensures preparedness and quick response to breaches. | Needs to be regularly updated, tested, and communicated. |
| Use of Security Features (e.g., IP Whitelisting) | High | Medium | Low | Restricts access and enhances overall security posture. | May require technical expertise; can impact usability if misconfigured. |
Conclusion: Strengthening Cybersecurity Measures
Recap of ShinyHunters’ Tactics
ShinyHunters have demonstrated the devastating impact of social engineering tactics on corporate cybersecurity. Their ability to exploit human vulnerabilities poses a significant threat to organizations worldwide. By understanding their methods, companies can better prepare and defend against similar threats.
Future Outlook on Cybersecurity
As cyber threats continue to evolve, companies must remain vigilant and proactive in enhancing their cybersecurity frameworks. By understanding the tactics of groups like ShinyHunters, organizations can better protect themselves against future attacks. This involves not only technological solutions but also fostering a culture of security awareness and resilience.
Practical Checklist for Defense
- Conduct regular security awareness training for all employees.
- Implement and enforce multi-factor authentication across all systems.
- Regularly update and patch software to close vulnerabilities.
- Utilize AI-driven tools for real-time threat detection.
- Schedule periodic security audits and incident response drills.
- Establish a clear protocol for reporting suspicious activities.
- Utilize Salesforce’s security features effectively.
- Stay informed about the latest cyber threats.
Leveraging Security Information and Event Management (SIEM) Solutions
Implementing a Security Information and Event Management (SIEM) solution can significantly enhance the ability to detect and respond to social engineering attacks. SIEM tools collect and analyze security data from across the organization, providing real-time insights and alerts for suspicious activities.
// Example: Configuring SIEM Alerts for Salesforce
Set up data connectors for Salesforce
Define alert rules for unauthorized access attempts
Enable real-time notifications for security teams
- Deploy a SIEM solution to centralize security monitoring.
- Configure alerts for unusual Salesforce login activities.
- Regularly review SIEM reports for potential threats.
- Integrate SIEM with existing security infrastructure.
Implementing Zero Trust Architecture
Zero Trust Architecture (ZTA) is a comprehensive security framework that requires verification of every user and device attempting to access resources on a network. By assuming that threats could exist both inside and outside the network, ZTA ensures that access is granted based on strict identity verification and continuous monitoring.
{
"zeroTrust": {
"verifyIdentity": "always",
"deviceCompliance": "required",
"accessControls": {
"leastPrivilege": true,
"sessionTimeout": "30 minutes"
},
"monitoring": {
"realTime": true
}
}
}
- Enforce identity verification for all users and devices.
- Implement least privilege access controls.
- Utilize continuous monitoring and real-time threat detection.
Tools like Okta and Microsoft Azure AD can help in implementing a Zero Trust framework by providing identity management and access control solutions.
Enhancing Email Security with DMARC
Domain-based Message Authentication, Reporting & Conformance (DMARC) is an email authentication protocol designed to give email domain owners the ability to protect their domain from unauthorized use, such as phishing and email spoofing. Implementing DMARC helps in verifying the authenticity of email senders and reducing the risk of email-based attacks.
v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]; pct=100;
- Publish a DMARC policy to protect your domain.
- Monitor DMARC reports to track and adjust email policies.
- Configure SPF and DKIM records to enhance email validation.
Popular tools for DMARC implementation and monitoring include DMARC Analyzer and Valimail.
Utilizing Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions are essential for identifying and mitigating threats at endpoint devices such as laptops, desktops, and servers. EDR tools provide real-time monitoring and response capabilities to detect suspicious activities and prevent potential breaches.
{
"EDR": {
"realTimeMonitoring": true,
"automatedResponse": true,
"threatIntelligence": "integrated"
}
}
- Deploy EDR solutions across all endpoint devices.
- Utilize real-time threat intelligence for proactive defense.
- Ensure automated response capabilities for rapid threat mitigation.
- Regularly update EDR software for optimal protection.
Notable EDR tools include CrowdStrike Falcon, Carbon Black, FortiEDR, etc. which offer comprehensive endpoint protection and threat detection features.
Implementing Zero Trust Architecture
Zero Trust Architecture (ZTA) is a comprehensive security framework that requires verification of every user and device attempting to access resources on a network. By assuming that threats could exist both inside and outside the network, ZTA ensures that access is granted based on strict identity verification and continuous monitoring.
{
"zeroTrust": {
"verifyIdentity": "always",
"deviceCompliance": "required",
"accessControls": {
"leastPrivilege": true,
"sessionTimeout": "30 minutes"
},
"monitoring": {
"realTime": true
}
}
}
- Enforce identity verification for all users and devices.
- Implement least privilege access controls.
- Utilize continuous monitoring and real-time threat detection.
Tools like Okta and Microsoft Azure AD can help in implementing a Zero Trust framework by providing identity management and access control solutions.
Enhancing Email Security with DMARC
Domain-based Message Authentication, Reporting & Conformance (DMARC) is an email authentication protocol designed to give email domain owners the ability to protect their domain from unauthorized use, such as phishing and email spoofing. Implementing DMARC helps in verifying the authenticity of email senders and reducing the risk of email-based attacks.
v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]; pct=100;
- Publish a DMARC policy to protect your domain.
- Monitor DMARC reports to track and adjust email policies.
- Configure SPF and DKIM records to enhance email validation.
Popular tools for DMARC implementation and monitoring include DMARC Analyzer and Valimail.
Enhancing Email Security with Advanced Threat Protection (ATP)
Advanced Threat Protection (ATP) solutions can help protect against email-based social engineering attacks by identifying and blocking malicious emails before they reach users. ATP focuses on detecting phishing attempts, malware, and other threats that exploit email communication.
// Example: Configuring ATP for Email Security
Enable ATP features in email services
Set up custom policies for phishing detection
Monitor ATP reports for ongoing threat analysis
- Enable ATP in your organization’s email systems.
- Customize ATP policies to identify phishing emails.
- Review ATP threat reports regularly for new insights.
- Ensure email filtering rules are up-to-date.
FAQs
What should I implement first?
Start with the highest-risk controls that provide quick wins, and iterate based on measurable outcomes.
How do I measure success?
Define KPIs tied to your objective: coverage, detection latency, false positives, MTTR, and business impact.
What are ShinyHunters known for?
ShinyHunters are known for their sophisticated social engineering tactics and have been linked to several high-profile cyber attacks on major corporations.
How can companies protect against social engineering?
Companies can protect against social engineering by educating employees, implementing robust security protocols, and utilizing advanced cybersecurity tools.
Why are Salesforce accounts targeted?
Salesforce accounts contain valuable customer data and business intelligence, making them attractive targets for cybercriminals.
How did Shinyhunters target Salesforce?
They used phishing attacks to compromise Salesforce accounts by capturing login credentials
What measures can prevent social engineering attacks?
Employee training, multi-factor authentication, and vigilant monitoring can help prevent social engineering attacks.
How can Salesforce’s security features be leveraged?
Salesforce provides IP whitelisting, session management, and audit logs that can be configured for enhanced security
Why are regular security audits important?
Regular security audits help identify vulnerabilities and ensure that security measures are effective and up-to-date.



